Why is AppSquadz your best partner for Cybersecurity?
Comprehensive Cybersecurity Solutions to Safeguard Your Business
The Advanced Cybersecurity Solutions we Offer for Today’s Digital ThreatsStay ahead of cyber breaches with our reliable cybersecurity services, delivering end-to-end protection, continuous monitoring, and proactive threat mitigation through managed security services designed for businesses of all sizes.
Our Impact and Recognition


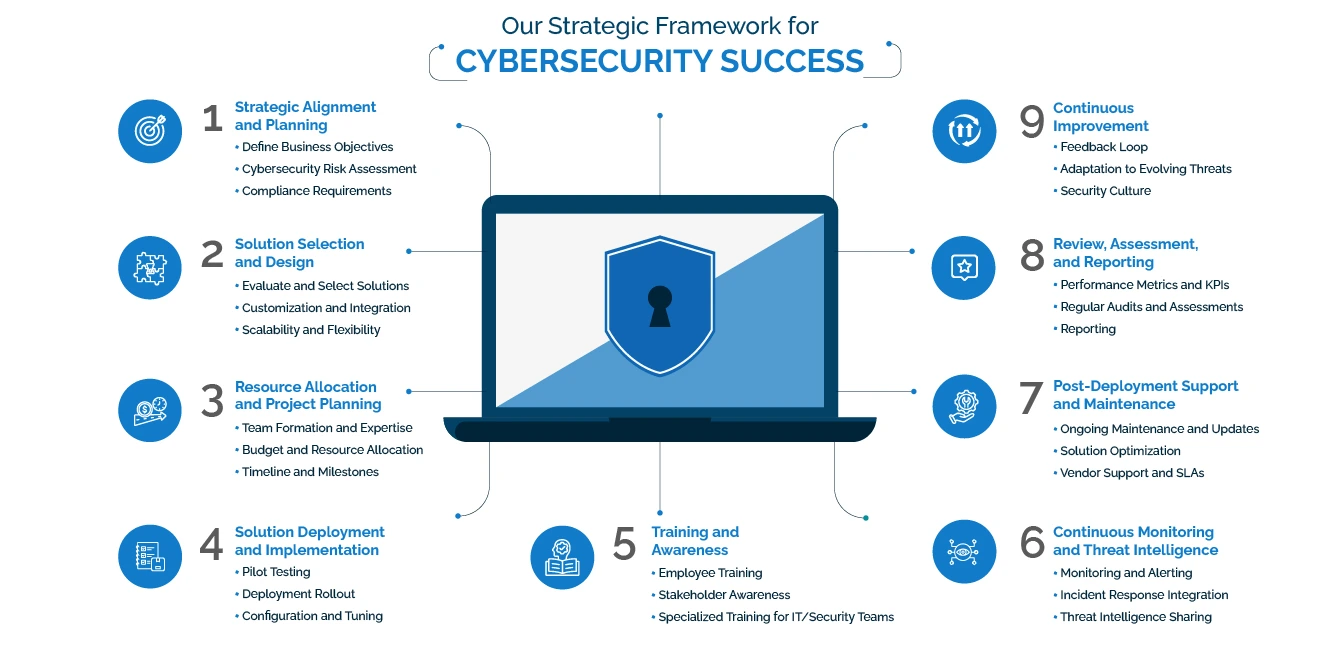
AppSquadz — Delivering Comprehensive Cybersecurity for a Secure Tomorrow
Cybersecurity has become a business-critical priority in today’s rapidly evolving digital landscape. Organizations must safeguard sensitive data, applications, and infrastructure against growing cyber threats through structured risk assessment services, robust endpoint security services, and scalable cloud security services. A proactive security approach is essential to reduce vulnerabilities, prevent breaches, and maintain operational continuity.
At AppSquadz, we deliver enterprise-grade cybersecurity services designed to protect businesses from data breaches, ransomware, and advanced threats. Our solutions integrate security and compliance services, continuous monitoring, threat detection and response, and reliable managed security services. We support startups to large enterprises with tailored strategies, ensuring regulatory readiness through regulatory compliance services while strengthening overall security posture.
Trusted Customers
The Advanced Cybersecurity Solutions We Offer for Today’s Digital Threats
We deliver comprehensive cybersecurity services by combining advanced technologies, expert-driven strategies, and proactive risk management to secure enterprise environments.
Network Security
Our network security solutions safeguard digital infrastructure using firewalls, VPNs, intrusion detection, and prevention systems. We help prevent unauthorized access, data breaches, and cyberattacks while ensuring reliable cloud & network security services.
Endpoint Security
We protect endpoints with antivirus, anti-malware, mobile device management (MDM), and endpoint detection and response (EDR). Our endpoint security services secure devices against advanced threats across distributed work environments.
Identity and Access Management (IAM)
We deliver identity and access management solutions, including MFA, role-based access control, and privileged access management. These capabilities support zero-trust security solutions by ensuring only authorized users have access to critical systems.
Cloud Security
Our cloud security services include CASB, CSPM, DLP, encryption, and comprehensive cloud infrastructure protection to secure cloud workloads while maintaining regulatory compliance.
Application Security
We embed security across the SDLC using WAF, SAST, DAST, and penetration testing, delivering reliable web application security solutions that protect business-critical applications.
Data Security
Our data security services focus on encryption, data masking, backup, disaster recovery, and integrity controls to protect sensitive information from unauthorized access and data loss.
Threat Intelligence & Management
We enable proactive defense using SIEM and SOAR platforms to deliver real-time threat detection and response, supported by advanced enterprise security monitoring.
Incident Response and Forensics
Our incident response services follow structured methodologies to contain breaches, investigate root causes, and restore operations through expert-led SOC support.
Compliance and Governance
We help organizations meet regulatory obligations through audits, governance frameworks, and ongoing cybersecurity compliance services aligned with GDPR, HIPAA, and PCI DSS.
Business Continuity and Disaster Recovery (BC/DR)
Our BC/DR services ensure rapid recovery of systems and data following cyber incidents, minimizing operational disruption.
Security Awareness Training
We train employees to recognize phishing, malware, and social engineering threats through simulations and awareness programs that strengthen human-layer security.
Physical Security
Our physical security solutions include access control systems and surveillance technologies to protect sensitive infrastructure and restricted environments.
Secure Your Business with Advanced Cybersecurity Services
Protect data, ensure compliance, and defend against evolving cyber threats proactively
We stand out as a trusted partner in delivering reliable, innovative, and industry-leading cybersecurity services.
Experienced Professionals
Our team comprises certified cybersecurity experts with a deep knowledge and understanding of the latest threats and technologies.
Tailored Security Strategies
We offer customized solutions that align with your unique business requirements and risk profile.
Customized Solutions
We customize our services and products to meet the specific needs of your business, ensuring optimal protection and performance.
Compliance Assurance
We aim that your business meets all relevant regulatory requirements to avoid fines and reputational damage.
Proactive Approach
We employ a proactive security strategy to prevent breaches before they occur, minimizing risks and potential losses.
Comprehensive Support
From initial consultation to ongoing support, we are with you at every step, providing unparalleled 24/7 service and expertise.
Frequently Asked Questions
We provide end-to-end cybersecurity services, including network, application, cloud, endpoint security, incident response, and compliance management.
Our experts perform detailed risk assessment services to identify vulnerabilities and recommend mitigation strategies.
Implementation timelines vary based on complexity, but our team ensures efficient deployment without compromising security.
Yes, we deliver tailored cybersecurity compliance services in India, supporting GDPR, HIPAA, and PCI-DSS requirements.
Yes, we provide fully managed security services with 24/7 monitoring, threat detection, and rapid incident response through expert SOC support.
Absolutely. Our cybersecurity solutions are designed to be scalable and flexible, supporting business growth, cloud expansion, and evolving security needs without disruption.
Get in Touch with Our Experts
Whether you have a project in mind, a query, or simply want to explore how we can collaborate, we’re here to help.
